If your on-premises datacenter is connected to Azure via ExpressRoute, you will be able to use Azure Private peering for connectivity to your private resources in your Azure VNets as well as Microsoft peering for connectivity to Azure public services.
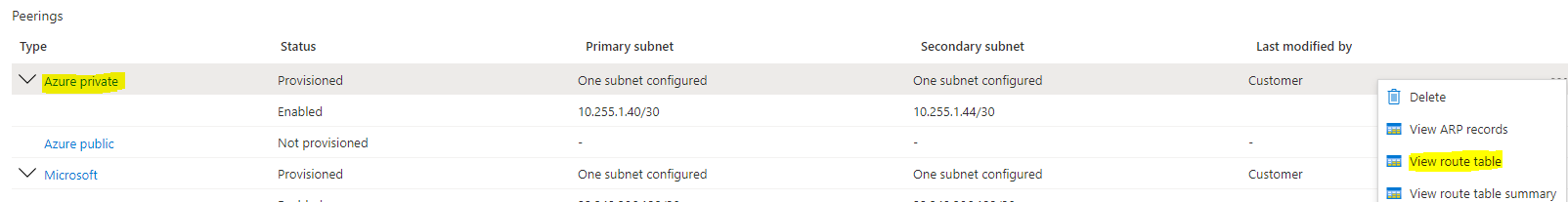
When troubleshooting connectivity between on-premises and your Azure private resources, you'd typically look at network routes and firewall policies, among other things. Given below are two ways to check if the relevant on-premises networks are visible on Azure (advertised via Azure Private peering) in its ExpressRoute circuit route table.
Azure Portal
Check the route table on the relevant ExpressRoute circuit circuit as shown in the screenshot below. You may also download the route table (as a csv) for both primary and secondary ExpressRoute circuit connections.
Azure CLI
Use the following command structure to view the route table JSON for both primary and secondary ExpressRoute circuit connections.
az network express-route list-route-tables -g <resource-group-name> -n <expressroute-circuit-name> --path <primary or secondary> --peering-name AzurePrivatePeeringFor example, to view the route table JSON for a primary connection on ExpressRoute circuit cg-erc in resource group cg-rg, use the following command:
az network express-route list-route-tables -g cg-rg -n cg-erc --path primary --peering-name AzurePrivatePeeringIn order to just obtain a convenient list of networks in the route table, you may add the additional --query switch as shown below:
az network express-route list-route-tables -g cg-rg -n cg-erc --path primary --peering-name AzurePrivatePeering --query 'value[].[network]' -o tsv